Integrating Next-Generation Outlets With Electronic Measurement Equipment
In the rapidly evolving landscape of electronic measurement, where precision and reliability reign supreme, the integration of next-generation outlets emerges as a pivotal frontier. As technology continues to advance, the demand for seamless connectivity and enhanced functionality becomes increasingly pronounced. Equipment to measure stands at the cusp of a new era, where traditional power outlets transcend their conventional roles to interface seamlessly. Below are details explaining the importance of integrating next-generation outlets with electronic measurement equipment and the benefits it can bring to your research endeavors.
Understanding Next-Generation Outlets

Next-generation outlets, often referred to as smart outlets, go beyond the traditional electrical connection by introducing advanced features. These intelligent outlets are designed to interconnect with a range of devices, allowing for enhanced control and monitoring capabilities. They are equipped with high-speed data transmission, wireless connectivity options, and programmable functionalities.
Advantages of Integrating Next-Generation Outlets
Improved Energy Efficiency: One significant advantage of smart outlets is their ability to optimize energy consumption. By integrating electronic measurement equipment with smart outlets, you can track and analyze power usage, identify inefficient devices, and make informed decisions to reduce energy costs.
Remote Monitoring and Control: With smart outlets, you gain the ability to monitor and control your electronic measurement equipment remotely through wireless connectivity. This feature proves invaluable, especially when dealing with time-sensitive experiments or managing equipment in multiple locations. You can receive real-time notifications, adjust settings, and ensure smooth operation, even from a distance.
Enhanced Safety Features: Traditional outlets have limitations when it comes to detecting faulty connections or electrical overloads. Next-generation outlets, on the other hand, offer advanced safety features such as surge protection, ground fault detection, and short-circuit prevention. By integrating electronic measurement equipment with smart outlets, you add an extra layer of safety to your lab environment.
Streamlining Data Management
By integrating smart outlets with electronic measurement equipment, you can simplify data management processes. Smart outlets enable the collection and analysis of data related to power consumption, temperature, humidity, and other environmental factors. This data can be seamlessly integrated into laboratory information management systems (LIMS) or other centralized platforms, providing researchers with a holistic view of their experiments.
Scalability and Flexibility

Next-generation outlets are designed for scalability, allowing labs to adapt as their needs evolve. The ability to add or remove outlets without rewiring or disrupting operations makes them ideal for accommodating changing experimental setups. Whether you need to expand your lab space, reconfigure equipment placement, or integrate additional devices, smart outlets provide the necessary flexibility.
Future-Proofing Your Lab
By embracing the integration of next-generation outlets with electronic measurement equipment, you future-proof your lab against rapidly evolving technology. Upgrading traditional outlets to smart outlets ensures compatibility with emerging devices and technologies, safeguarding your investments for the long term. This proactive approach enables labs to stay at the forefront of scientific advancements while maximizing the efficiency and accuracy of their research.
In an era of continuous technological innovation, laboratories must keep pace with the latest advancements to remain competitive. By adopting this …



 DHCP, also known as Dynamic Host Configuration Protocol, is a fundamental networking protocol that plays a crucial role in enabling devices to connect to a network and obtain necessary IP configurations automatically. It simplifies the process of assigning IP addresses, subnet masks, default gateways, and other network parameters to devices within a network.
DHCP, also known as Dynamic Host Configuration Protocol, is a fundamental networking protocol that plays a crucial role in enabling devices to connect to a network and obtain necessary IP configurations automatically. It simplifies the process of assigning IP addresses, subnet masks, default gateways, and other network parameters to devices within a network.



 Let’s dive into the first step – extraction. It involves gathering and analyzing data from a target system to gain insights into its inner workings. This process requires careful observation, documentation, and investigation. To begin with, you need to thoroughly examine the software or hardware you wish to reverse engineer. Take note of its features, functions, and any visible patterns. This initial analysis will help you understand how different components interact with each other.
Let’s dive into the first step – extraction. It involves gathering and analyzing data from a target system to gain insights into its inner workings. This process requires careful observation, documentation, and investigation. To begin with, you need to thoroughly examine the software or hardware you wish to reverse engineer. Take note of its features, functions, and any visible patterns. This initial analysis will help you understand how different components interact with each other.
 Once you have completed the modeling stage of reverse engineering, it is time to move on to the review phase. This is a crucial step where you evaluate and analyze your findings. During the review process, take a close look at the extracted information and the models you have developed. Check for any inconsistencies or errors that may have occurred during the extraction or modeling stages.
Once you have completed the modeling stage of reverse engineering, it is time to move on to the review phase. This is a crucial step where you evaluate and analyze your findings. During the review process, take a close look at the extracted information and the models you have developed. Check for any inconsistencies or errors that may have occurred during the extraction or modeling stages.
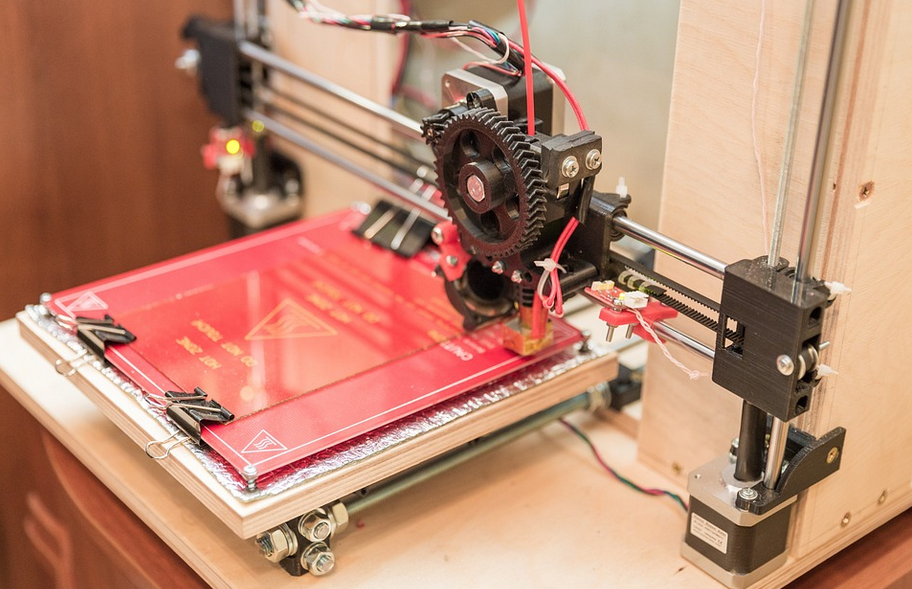
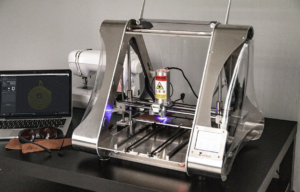 The last trend we will discuss is sustainability. As the world becomes increasingly aware of the environmental impact of traditional manufacturing methods, more and more people are turning to 3D printing to reduce their carbon footprint. 3D printers use less material than traditional manufacturing methods, making them much more eco-friendly. Additionally, 3D-printed objects can be recycled and reused, making them a great way to reduce waste. 3D printing is also often used to produce biodegradable materials, reducing its environmental impact. Many companies are now embracing 3D printing in their sustainable production processes, and this trend will likely continue to grow.
The last trend we will discuss is sustainability. As the world becomes increasingly aware of the environmental impact of traditional manufacturing methods, more and more people are turning to 3D printing to reduce their carbon footprint. 3D printers use less material than traditional manufacturing methods, making them much more eco-friendly. Additionally, 3D-printed objects can be recycled and reused, making them a great way to reduce waste. 3D printing is also often used to produce biodegradable materials, reducing its environmental impact. Many companies are now embracing 3D printing in their sustainable production processes, and this trend will likely continue to grow.
 One of the most critical keys to high-traffic
One of the most critical keys to high-traffic  Ultimately, your mobile app needs to be easy to use. People will quickly get frustrated and stop using it if it’s not. One of the most critical aspects of ease-of-use is navigation. Your app needs to have a clear and intuitive navigation system. People should be able to find what they’re looking for without trouble. If your app is difficult to navigate, you’re going to lose a lot of users.
Ultimately, your mobile app needs to be easy to use. People will quickly get frustrated and stop using it if it’s not. One of the most critical aspects of ease-of-use is navigation. Your app needs to have a clear and intuitive navigation system. People should be able to find what they’re looking for without trouble. If your app is difficult to navigate, you’re going to lose a lot of users.
 A gaming headset is a must-have for any gamer. If you want to get the most out of your gaming experience, then you need to be able to hear everything that is going on around you. A good gaming headset will provide you with surround sound and clear audio to hear every footstep and explosion. Plus, they can also help to reduce noise and distractions so that you can focus on the game. In addition to providing great audio, gaming headsets can also provide features such as LED lighting, vibration, and microphone control.
A gaming headset is a must-have for any gamer. If you want to get the most out of your gaming experience, then you need to be able to hear everything that is going on around you. A good gaming headset will provide you with surround sound and clear audio to hear every footstep and explosion. Plus, they can also help to reduce noise and distractions so that you can focus on the game. In addition to providing great audio, gaming headsets can also provide features such as LED lighting, vibration, and microphone control. An ergonomic chair is another must-have for any gamer. If you are going to spend hours playing video games, you need to be sitting in a comfortable and supportive chair. An ergonomic chair will help reduce fatigue and pain, so you can game for longer without feeling uncomfortable. In addition to being comfortable, an ergonomic chair can also be adjustable, so you can find the perfect fit for your body.
An ergonomic chair is another must-have for any gamer. If you are going to spend hours playing video games, you need to be sitting in a comfortable and supportive chair. An ergonomic chair will help reduce fatigue and pain, so you can game for longer without feeling uncomfortable. In addition to being comfortable, an ergonomic chair can also be adjustable, so you can find the perfect fit for your body. If you want to get the most out of your gaming experience, you need to use a good set of stereo speakers. Compared to traditional laptop speakers, stereo speakers will provide you with superior sound quality and clarity. This is essential for enjoying immersive and realistic gaming audio. For instance, if you are playing a game that has sound effects and music, then you will be able to hear them much more clearly with stereo speakers. In addition to enhancing your gaming audio, stereo speakers can also improve your overall audio experience when listening to music and movies.
If you want to get the most out of your gaming experience, you need to use a good set of stereo speakers. Compared to traditional laptop speakers, stereo speakers will provide you with superior sound quality and clarity. This is essential for enjoying immersive and realistic gaming audio. For instance, if you are playing a game that has sound effects and music, then you will be able to hear them much more clearly with stereo speakers. In addition to enhancing your gaming audio, stereo speakers can also improve your overall audio experience when listening to music and movies.
 The first step to choosing the best online computer game is making sure it works with your PC. Ensure you go over the system requirements for whatever game you are considering downloading or buying. If a game says that it needs at least an Intel Core i-2300 processor, then that means if your laptop only has an AMD E-450 processor, then the game probably isn’t compatible with your computer.
The first step to choosing the best online computer game is making sure it works with your PC. Ensure you go over the system requirements for whatever game you are considering downloading or buying. If a game says that it needs at least an Intel Core i-2300 processor, then that means if your laptop only has an AMD E-450 processor, then the game probably isn’t compatible with your computer. Online reviews will give an idea of what to expect when playing certain game titles and how they compare to similar ones available in the industry. While some players may not find time to read each one, there is no harm in looking at them before buying any latest game.
Online reviews will give an idea of what to expect when playing certain game titles and how they compare to similar ones available in the industry. While some players may not find time to read each one, there is no harm in looking at them before buying any latest game.



 You must know the basics of these records. Almost all Android users are not fully aware of the importance and result of APK files. Even though it is a simple fact that we dwell on APK files from time to time with no small amount, it can still be very valuable to find out just in case you would need them later on in case you want to download more applications for your Android device. APK files are already in the software found in the Android Market.
You must know the basics of these records. Almost all Android users are not fully aware of the importance and result of APK files. Even though it is a simple fact that we dwell on APK files from time to time with no small amount, it can still be very valuable to find out just in case you would need them later on in case you want to download more applications for your Android device. APK files are already in the software found in the Android Market.




 Major monitoring children applications offer many facilities, such as time limitation and harmful words, images, and videos on the children’s device. It also helps to monitor behavior while keeping the children’s privacy. Another usage involves location monitoring and various applications limitation when it is essential.
Major monitoring children applications offer many facilities, such as time limitation and harmful words, images, and videos on the children’s device. It also helps to monitor behavior while keeping the children’s privacy. Another usage involves location monitoring and various applications limitation when it is essential.  This app has all the features a parent can request as their mobile gadget management provider. It also can control many services on various gadgets. Sure, a parent cannot handle to spy 24 hours of their child’s mobile usage. Still, parents are at ease with having proper control app to ensure their child fairly uses their gadgets with the help of all the features they offer, such as application monitoring, web filtering, and location.
This app has all the features a parent can request as their mobile gadget management provider. It also can control many services on various gadgets. Sure, a parent cannot handle to spy 24 hours of their child’s mobile usage. Still, parents are at ease with having proper control app to ensure their child fairly uses their gadgets with the help of all the features they offer, such as application monitoring, web filtering, and location. 
 The program is undetectable by the individual in whose phone it’s been presented. It’s an establishment that completed the
The program is undetectable by the individual in whose phone it’s been presented. It’s an establishment that completed the 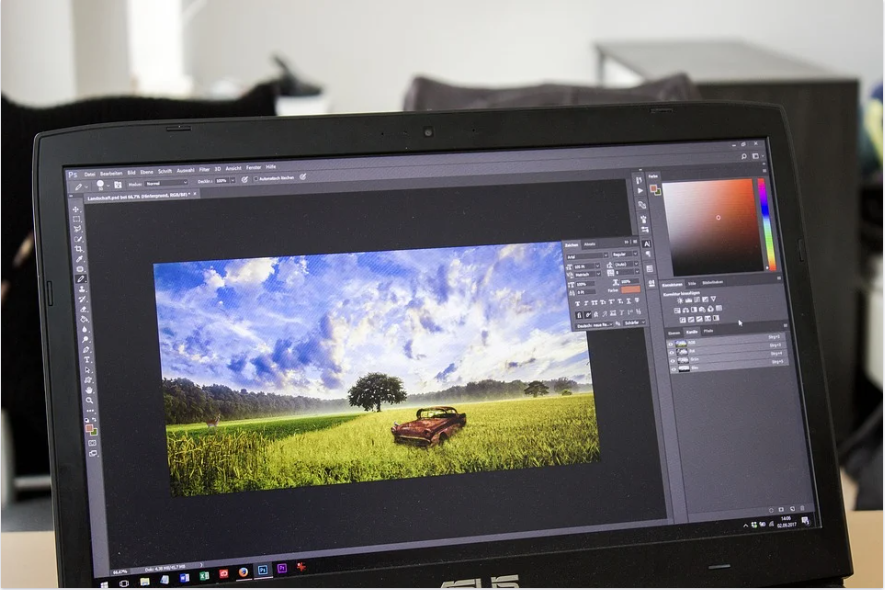

 Color space controls in Lightroom help you solve the most common color problems. Using the white balance controls, including the Temp and Tint sliders, neutralizes unwanted color casts and makes the colors look more realistic. If a photo’s color looks dull, make them more intense with the Vibrance or Saturation sliders.
Color space controls in Lightroom help you solve the most common color problems. Using the white balance controls, including the Temp and Tint sliders, neutralizes unwanted color casts and makes the colors look more realistic. If a photo’s color looks dull, make them more intense with the Vibrance or Saturation sliders.
 It usually means that the consumer takes full responsibility for that machine. Besides, all server hardware and software tools are fully utilized on the customer’s website. This form of hosting brings fantastic benefits, which makes it so important for certain types of organizations. It usually depends on the total amount of website traffic. It depends on how bandwidth selects the amount of data transferred from the server to the website and vice versa in a given period.
It usually means that the consumer takes full responsibility for that machine. Besides, all server hardware and software tools are fully utilized on the customer’s website. This form of hosting brings fantastic benefits, which makes it so important for certain types of organizations. It usually depends on the total amount of website traffic. It depends on how bandwidth selects the amount of data transferred from the server to the website and vice versa in a given period. The amount of memory that the website requires. Before choosing a hosting company for a dedicated server, the website operator should consider the website’s memory requirements and how this may affect its loading speed. RAM is the data storage capacity available to allow website visitors to receive all their computer information. Therefore, the more RAM a website has, the faster it loads.
The amount of memory that the website requires. Before choosing a hosting company for a dedicated server, the website operator should consider the website’s memory requirements and how this may affect its loading speed. RAM is the data storage capacity available to allow website visitors to receive all their computer information. Therefore, the more RAM a website has, the faster it loads.